In the rapidly evolving landscape of cybersecurity, a new player has emerged that challenges conventional understandings of digital safety: the O.MG Cable. This seemingly innocuous device, mirroring the appearance of standard USB cables, conceals a potent threat to data security. This article aims to demystify the O.MG Cable, elucidate the risks it poses, and provide practical advice for safeguarding against such threats.
What is the O.MG Cable?
The O.MG Cable, at first glance, appears to be a typical USB cable used for charging or transferring data. However, its ordinary facade masks a sinister capability. These cables have been clandestinely modified to incorporate hardware enabling unauthorized remote access to devices. Designed initially for security research, they have unfortunately found their way into the arsenal of cybercriminals.
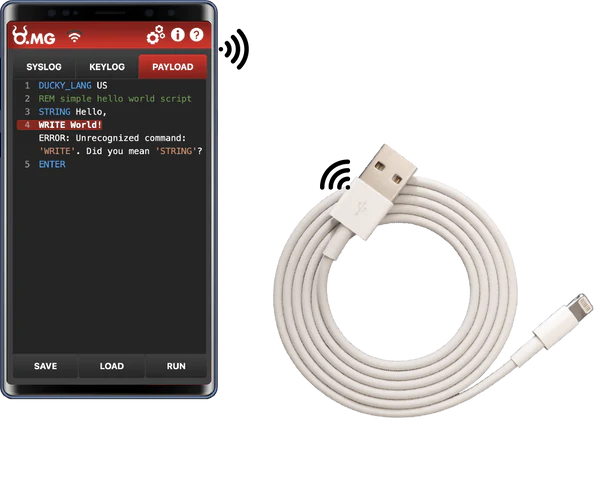
Capabilities and Threats
Remote Access
The O.MG Cable establishes a covert connection between the device and a hacker-controlled server, unbeknownst to the user. This breach enables cybercriminals to execute a range of malicious activities on the connected device.
Keystroke Logging
One of the most concerning features of the O.MG Cable is its ability to record every keystroke made on the connected device. This capability exposes sensitive information, including passwords and credit card details, to unauthorized access.
Screen Mirroring and Control
Cybercriminals can remotely monitor and control the device’s screen activities, accessing private messages, personal files, and even recording video calls without the user’s consent.
Spreading Malware
Beyond direct hacking, O.MG Cables can disseminate malware to further compromise system or network security.
Detection and Prevention Strategies
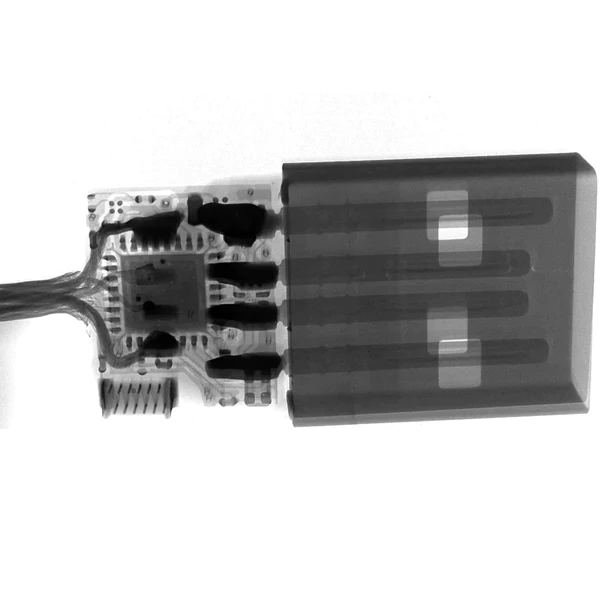
Detecting an O.MG Cable can be challenging due to its deceptive design. However, there are subtle differences:
- Notches and Finish: Apple’s genuine cables lack any impressions or notches and use a more matted metal finish, as opposed to the shinier finish of O.MG Cables.
- Communication Pins: The pins in genuine cables are thinner compared to those in O.MG Cables.
- Physical Examination: A small notch on the back and a seam on the side of the O.MG Cable might be noticeable upon close inspection.
To mitigate these risks, consider the following measures:
- Purchase from Reputable Sources: Buy USB cables only from authorized sellers or reputable sources.
- Regular Inspection: Examine the packaging and physical appearance of USB cables for signs of tampering.
- Utilize Security Software: Employ robust antivirus software that can detect threats posed by O.MG cables.
- Exercise Caution: Refrain from using USB cables from unknown sources or accepting them from strangers. Avoid charging devices at public USB ports.
Navigating the New Threat Landscape
The advent of the O.MG Cable represents a significant shift in the cybersecurity threat landscape. It underscores the need for heightened vigilance and proactive measures in protecting digital assets. Awareness and education are key in combating these evolving threats. By understanding the nature of these cables and implementing strategic defenses, individuals and organizations can significantly reduce their vulnerability to such insidious attacks.
In our digital age, where technology permeates every facet of our lives, the O.MG Cable serves as a stark reminder of the ever-present cyber threats. Staying informed and adopting comprehensive security measures are imperative in safeguarding against these sophisticated attacks. Remember, in the realm of cybersecurity, knowledge and vigilance are your strongest allies.